How to Connect to a Public WiFi Network
Connect to a Public [unsecured] WiFi network from a laptop or tablet. There are a few things to consider, when connecting to Public WiFi. Is it secured? An icon overlay showing an exclamation point inside of a shield denotes an unsecured Public network connection. Special care should be taken, when connecting to this type of WiFi. Even though you might have to enter a log on password, read a privacy statement and accept a Terms and Conditions agreement in order to connect, information shared over this type of connection might be viewable to others; such as document and internet surfing history, user names & passwords. Windows (Microsoft) is networking software; meaning that files, folders, printers and other devices can be shared with others in either an Office or Home Group environment. You can disable sharing, but this still isn't enough! Using a secure Browser such as Tor (The Onion Router) will keep your browsing history secret by providing "anonymity on the Internet." Still, you'll need to make changes to your surfing habits in order to secure that anonymity. Using a personal VPN (Virtual Private Network) to encrypt data information on public WiFi networks can prevent sophisticated hackers from tracking, monitoring or intercepting your web activities. Are you ready to connect?
Things You'll Need:
A WiFi-capable Laptop or Tablet
Things You'll Need:
A WiFi-capable Laptop or Tablet
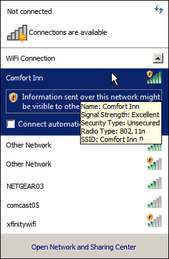 Available Wireless Connections Available Wireless Connections
1. Click the icon next to the clock, in the lower right-hand corner of your screen, which looks like cellphone reception bars. This opens a window showing all of the available wireless connections within range. On tablets, you will see available wireless networks, once you go into the Settings menu and click on WiFi.
If you have never connected through WiFi before and do not see this icon, check to be sure that your Laptop has built-in capability; some older models do not. In Windows Help (F1) search the term "Enable or disable a network adapter." Click the first link Enable or disable a network adapter. In the results, Click to open Network Connections. If equipped, you will see your Wireless Network Adapter listed. [If not, you will need to purchase a USB Network Adapter.] Right-click on your adapter and check to see that it is enabled. Click on Connect / Disconnect to open the adapter interface showing available connections.  Additional Log On Info Additional Log On Info
2. Connecting to an unsecured network may require a temporary password or passphrase. When you click on an available network which you intend on connecting to again, check the box to connect automatically [when it is in range]. If the network is non-secured, the check box is empty by default. Although you may see a flag notification in the lower right-hand corner of your screen stating that more action may be required to connect, wait before opening your browser. A window titled Set Network Location should open next. Wait for this window and set the connection type, before opening an internet browser.
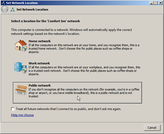 Set Network Location Set Network Location
3. Set the Network Location. When you connect to any WiFi network for the first time, Windows will prompt you to identify which type of network it is. Each type of wireless network, Home, Work and Public, requires different levels of security. This sets the appropriate level of firewall protection for that type of connection. Read and aknowledge the protection provided for the type of network you have selected. At this point, you now have an active connection which allows for Windows and your Antivirus protection program's to auto-update. Close the Network Location window.
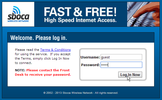 Log On Log On
4. Open your browser. Your browser should open or redirect to a page showing the User agreement/Terms of Use for the wireless network you have connected to. You may have to refresh the page (Fn+F5) before this representative page appears. Once you click to accept, a persistent cookie is then deposited in your temporary Internet History cache. This cookie must be allowed in order to remain connected. If you prefer to use a secure browser such as Tor, you must initially sign in using another browser (Firefox, Chrome, Internet Explorer, etc.), since Tor does not allow cookies as part of their anti-tracking security protocol.
Tips:
* Tor (The Onion Router) is a secure internet browser. * Use personal VPN software, such as CyberGhost VPN, to encrypt your data transmissions. * Wired connections transfer data faster than wireless. Even so, desktop computers can go wireless too! Warnings: * Information shared across non-secured wireless networks may be visible to others. * With each program exception (open port) you add to your Firewall, you create another possible entry-point for Hackers to exploit! Copyright 08/06/2014 All Rights Reserved. Questions? Comments? Contact Me Related Articles: Computer/Internet |
#ad |
